Signals
Prelude’s machine learning models use a number of signals to distinguish fraudulent users from legitimate users. We infer some of these signals, but many depend on the information provided by your integration. The more data you provide, the more effective fraud prevention will be and the higher your conversion rate will be.Important signals to send to Prelude
To increase the effectiveness of fraud prevention, we recommend that you send the following signals to Prelude:| Data | Estimated improvement | Description |
|---|---|---|
| IP address | 50% | The public IP v4 or v6 address of the end-user’s device. You should collect this from your backend. If your backend is behind a proxy, use the X-Forwarded-For, Forwarded, True-Client-IP, CF-Connecting-IP or an equivalent header to get the true public IP of the end-user’s device. |
| Device ID | 40% | A unique ID for the user’s device. You should ensure that each user device has a unique device_id. Ideally, for Android, this corresponds to the ANDROID_ID and for iOS, this corresponds to the identifierForVendor. |
| Platform | 35% | The platform of the user’s device (iOS or Android). |
| JA4 fingerprint | 30% | The JA4 TLS fingerprint observed for the user’s connection. Prelude will infer it automatically when you use our Frontend SDKs (which use Prelude’s edge network), but you can also forward the value if you terminate TLS yourself. |
| Device model | 20% | The model of the user’s device. |
| OS Version | 20% | The version of the user’s device operating system. |
| App version | 10% | The version of your application. |
Inferring signals from the User-Agent
Some signals can be inferred from the User-Agent string if you provide it to us:- Platform
- Device model
- OS version
os_version, device_platform, device_model) are provided, they will take precedence over those values instead of parsing them from the user agent string.
Adding more signals using our Frontend SDKs
You can add more signals that are collected directly from the user’s device using our Frontend SDKs.Android SDK
Learn how to integrate the Android SDK into your application.
iOS SDK
Learn how to integrate the iOS SDK into your application.
Web SDK
Learn how to integrate the Web SDK into your application.
React Native SDK
Learn how to integrate the React Native SDK into your application.
Flutter SDK
Learn how to integrate the Flutter SDK into your application.
Selectively bypassing the anti-fraud system
You can use theis_trusted_user signal to completely bypass the antifraud system for a specific verification request.
This field should indicate the trustworthiness of the user on your app, beyond just a basic validity check. It should ensure trust by confirming that the user is genuine within the context of your application. Examples of validation criteria include whether the user has completed onboarding steps, performed valid transactions, or completed a purchase.
When set to true, this will bypass fraud checks for that user.
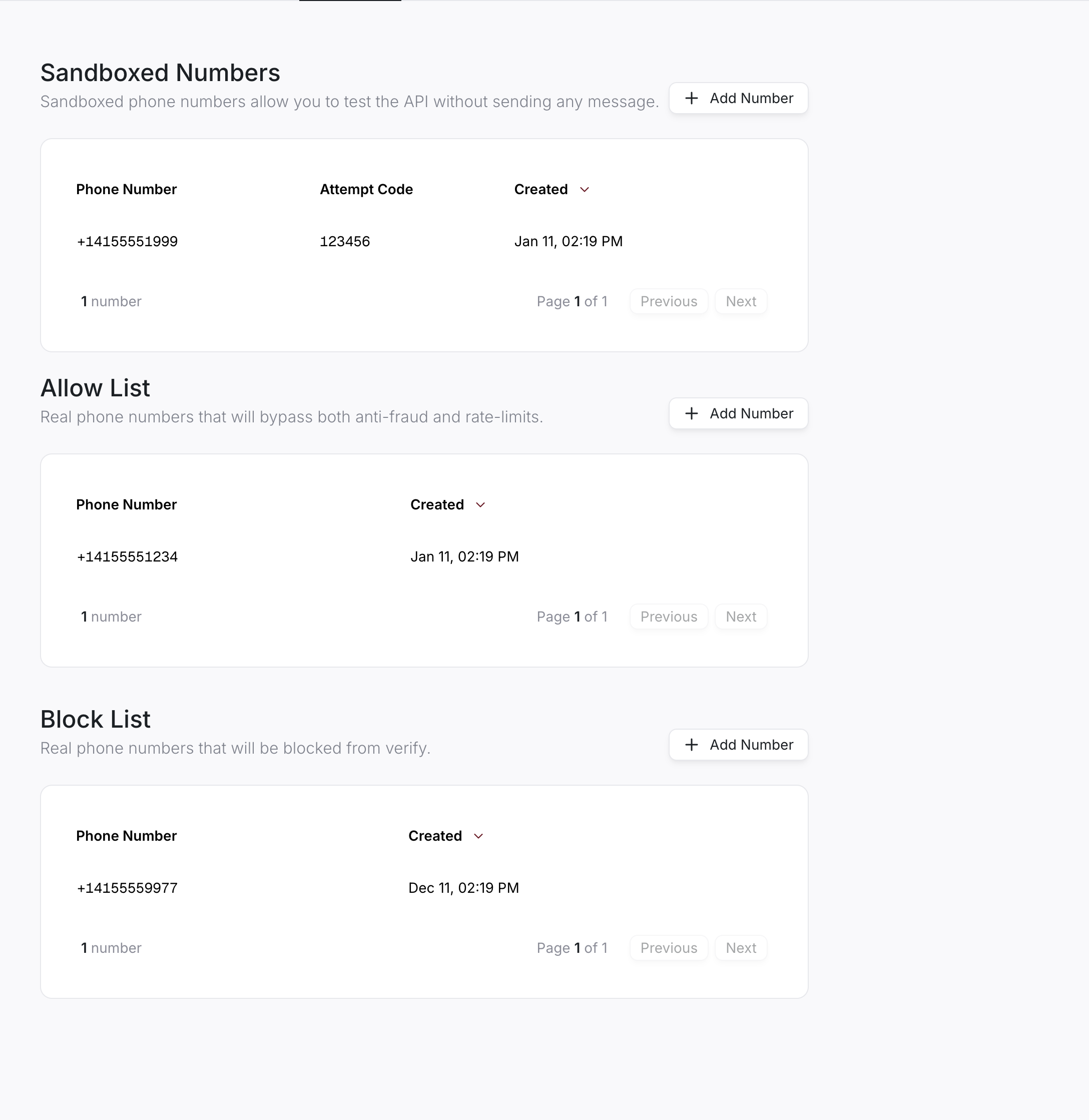
Allow and block lists
You can configure your integration to allow or block specific users from signing in. This can be useful if you want to manually block users you have identified as fraudulent or to disable anti-fraud algorithms for specific users. To edit the allow or block lists, go to the Dashboard and navigate to the Verify API > Configure > Numbers tab.